WOMBAT Project Description
Why research in emerging security threats ?
Today, combating cyber-crime becomes increasingly hard, for multiple reasons. The following observations in particular hightlight this trend:- Malware is designed to defeat today's best practices, both technologically, economically and sociologically.
- Organizations are consolidating malicious activities into profitable professional endeavors.
Project Motivation
The WOMBAT project aims at providing new means to understand the existing and emerging threats to the Internet infrastructure and the services this infrastructure supports.The WOMBAT project is organized around 3 activities:
- Real-time gathering of a diverse set of security-related raw data. WOMBAT will take advantage of existing data collection efforts undertaken by its partners or collaborating organizations. It will focus on leveraging existing tools and exploring the development of tools dedicated to wireless (wifi, RFID, Bluetooth) networks.
- Data enrichement by means of various analysis techniques. WOMBAT will formalize threat context information.
- Threat analysis. WOMBAT will build upon the information correlation expertise of its partners to provide root cause analysis. This will provide root cause identification and understanding of the phenomena under scrutiny, potentially leading to the establishment of early warning systems.
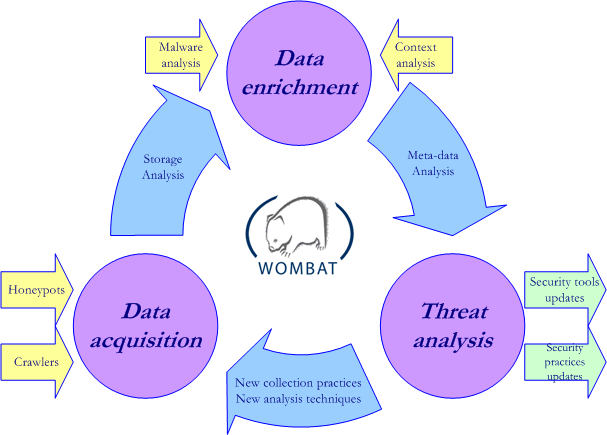
- Data collection: The WOMBAT project focuses on new collection mechanisms (e.g. extended crawlers, wireless honeypots) and on interoperability with existing efforts.
- Malware analysis: This activity regroups partner's works on malware analysis, either from a theoretical standpoint (grammars, formal models) or from a practical standpoint (taint analysis, flow analysis, ...).
- Context analysis: This activity aims at understanding the contextual information surrounding the malware, including but not limited to its provenance, its resemblance to other strains, its activity, its targets, etc.
- Threat analysis: The WOMBAT project aims at helping information security professionals update their software tools (e.g. detection signatures) and practices to the threats.
Project users
The acquired knowledge will be shared with all interested security actors (ISPs, CERTs, security vendors, etc.), enabling them to make sound security investment decisions and to focus on the most dangerous activities first. Special care will also be devoted to impact the level of confidence of the European citizens in the net economy by leveraging security awareness in Europe thanks to the gained expertise.For more information see contacts point.